Cybersecurity Services Capabilities

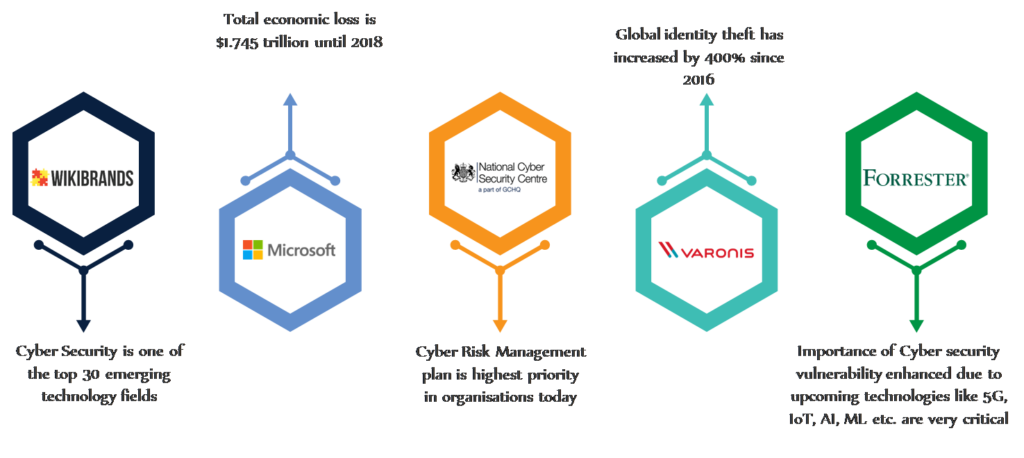
Why Security is talk of the day and Oppurtunity?
Mission
Priamba Mission is to offer value proposition to Government, Law Enforcement Agencies and Surveillance at critical infra as well as security agencies & enterprises to:
- Manage situations using integrated crime analysis tools in an automated ‘National / Enterprise level intelligence and security alerts and monitoring system’ comprising of several probes into critical areas with mass accumulation of data and automated prioritization of events to trigger an alert with consistent follow-up to prevent & monitor all possible subversive activities, anti-law activities.
- Integrate, yet cater to local needs of respective Units of Enterprises & Statutory bodies at National , State as well as Domestic levels to work in Synchronization.
- Application of SMART architecture to achieve the objectives with a set of sensors + probes etc. at the field level – leading to Enterprise / National level monitoring at Top level (central control) in a comprehensive manner with set of trained + skilled work force to tackle threats
360 degree coverage for Security needs
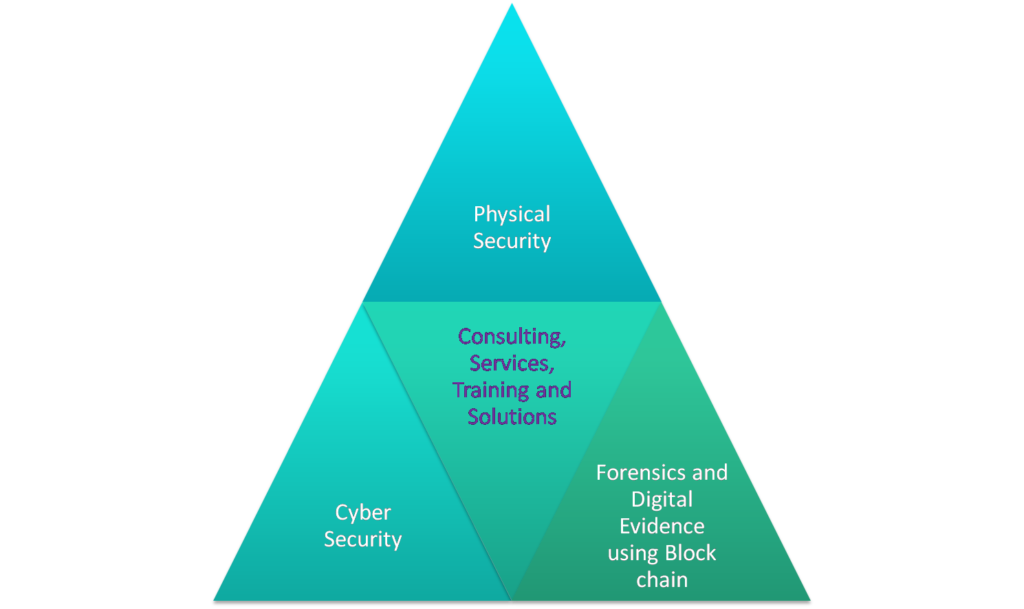
Cyber Security Offerings

4 Pillars – Physical and Cyber Security
Training
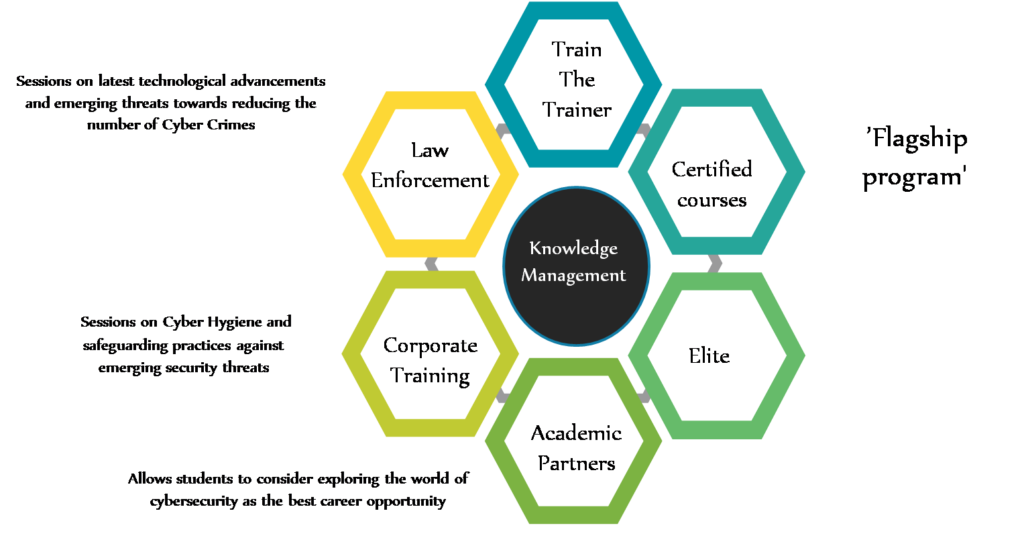
Enterprise-wide program – Track 1
- One-day orientation for Sr. Management and Executive Members
- 5-6 hr track in a nice environment for focused training
- Need for 360 degree view of security including Physical and Cyber Security
- Few historic incidents, where companies have lost money and data
- Security vs. Brand Identity
- Security Risks and assessments
- How to prevent incidents with emphasis
- PEOPLE + PROCESS + TECHNOLOGY ….
- Legal perspective – IT Laws / Cyber Compliance and Regulations
Enterprise-wide program – Track 2
- One-day orientation for Non-IT staff (end-users), including support staff and security personnel
- Protecting Digital Assets: Almost every recent research studies and data breach investigation reports reveal that the most common threat to information security and data confidentiality come from within an organization – its employees. In most cases, incidents were triggered by inadvertent actions of unsuspecting employees, typically by visiting websites infected with malware or Trojan, by responding to phishing e-mails, or even giving out sensitive information when confronted by social engineering attacks or use of cloud to keep copies or use of USB drives etc..
- This awareness program exposes target employees to modus operandi and prevailing threat landscape. The training not only help employees more resilient to security threats but also reduce the burden on the incident response team considerably. Training employees on good cyber hygiene prevents them from being breached outside their office environment as well, and thus contributing to a secure social environment.
Enterprise-wide program – Track 3
- 3 day hands-on + theory training to IT Staff of enterprises / department
- Just day after training, can implement systems and processes to improve security
- Exposure in boot-camp style to 30+ tools that can be used to
- Assess
- Predict
- Detect
- Protect
- The IT Assets and Infrastructure of the enterprise – without major IT investment
- Can be organised in the client location or campus of academic institutes
IT Security – Certificate course (Basic)
For IT related and Risk management teams
- “Certified Cyber Warrior” (CCW) from CCSER can help you start the journey of setting processes within organization
- Certification course specifically tailor-made for Banking & FI and e-Gov professionals who are revolutionizing Digital enablement plans
- The foundation course will enable participants to get ready for future advance courses like:
- Cyber Defender – Enterprise
- Intrusion Detection In-Depth
- Cyber Defender – Cloud computing
- Web App Penetration Testing and Ethical Hacking
- IOT Security Essentials
- Cyber Forensics and Investigations
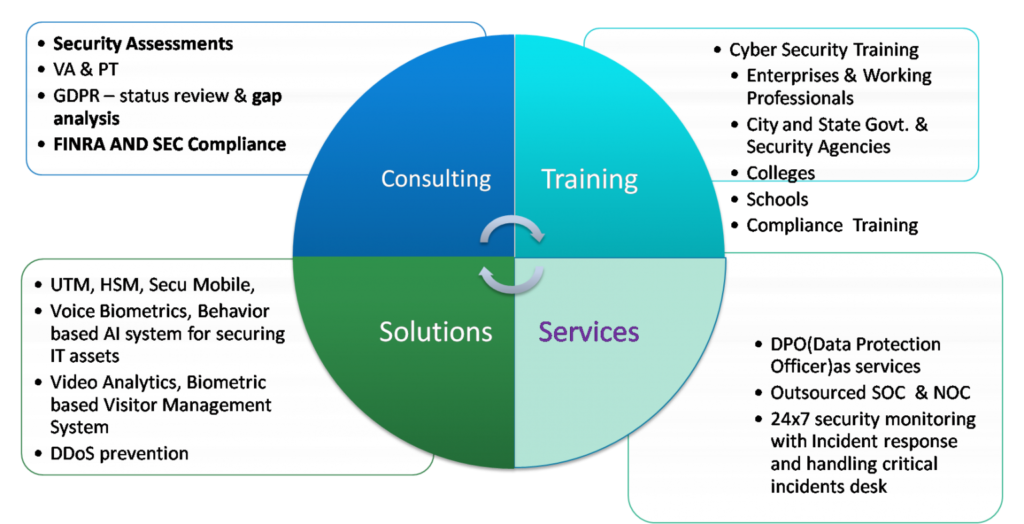
Wide Range of Solutions lined-up
Consulting
- Governance, Risk and Regulatory (GDPR)
- Compliance including Audit and Gap Analysis
- Application Security
- VA and PT
- Digital Forensics
- Cyber Insurance Readiness
- Incident Management
- Incident Handling
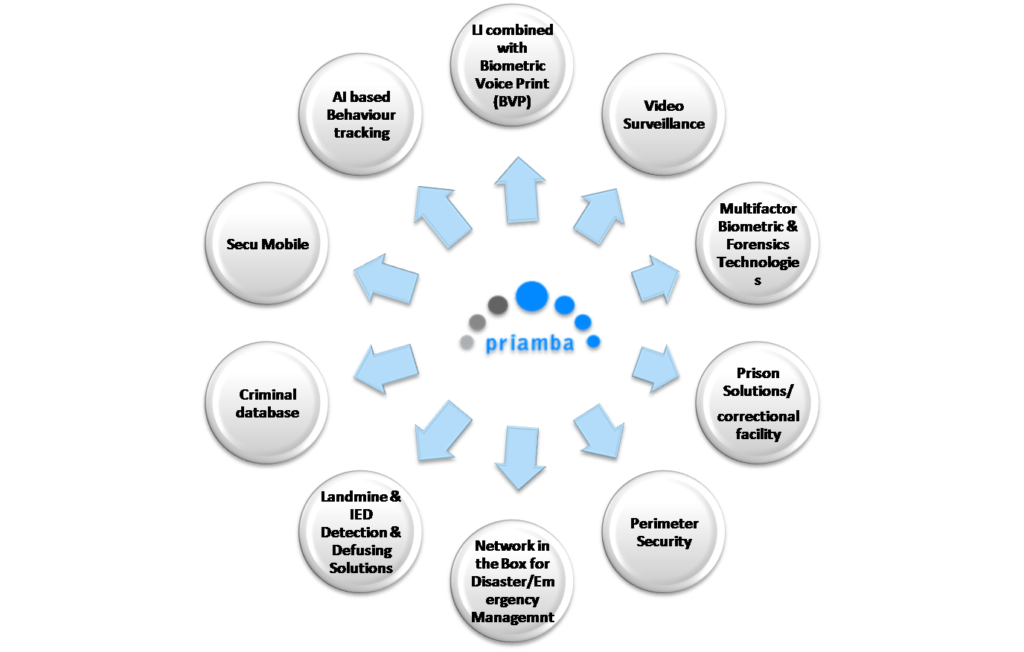
Solutions
Legal Interception Technology combined with Biometric Voice Print (BVP
- Spot target suspects and do a clustering as well link analytics.
- Aid in the fraudster detection in the call centres of the financial institutions.
- This is offered in association with expertise from USA and Spain, who have helped leading Intel organisations & Prosecutor’s offices world-wide etc.
Video Surveillance
- Image based recognition of Blacklisted and VIP detection and related intelligence including Forensics.
- CCTV Search of relevant content
- Media search by key people recognition
- Offered in association with companies from USA & Germany
Multi-factor Biometric and Forensics technologies
- Use the Voice + Face + Finger Print recognition for courts to prosecute the person.
- MOBIMASS for mobile authentication
- KWS & STT for linkage + clustering
- This is offered in association with companies from Czech, Sweden, Spain and UK
Prison/Correctional Facilities Solutions
- Post-prosecution, contraband cell phone detection, cell phone interception and tracking of criminals on the parole etc.
- This is offered in association with companies from USA
Perimeter Security
- Using Geo + Acoustic sensors with cueing to Video cameras and UAVs
- For sensitive installations like Refineries, Nuclear power plants and VVIP residences
- This is offered in association with companies from USA
Land mine & IED Detection and defusing Solutions
- Detection and defusing of IED and Landmines in the un-friendly terrains as well as naxal infested areas using UAVs and sensors including audio processing.
- This is offered in association with Companies from USA
Network-In-The-Box (NITB)like FEMA (Emergency Management agencies
- For emergency communication as well as disaster management sites without a public network and backhaul for use of Intelligence as well as rescue agencies etc.
- This is offered in association with companies from USA and Germany
Criminal database applications
Help Law enforcement agencies build database of criminals with centralized data sharing and analysis.
To counter criminal activities as well as cross border terrorism / act of violence.
This is offered in association with Companies from USA and built in-house in India.
Data Center Services
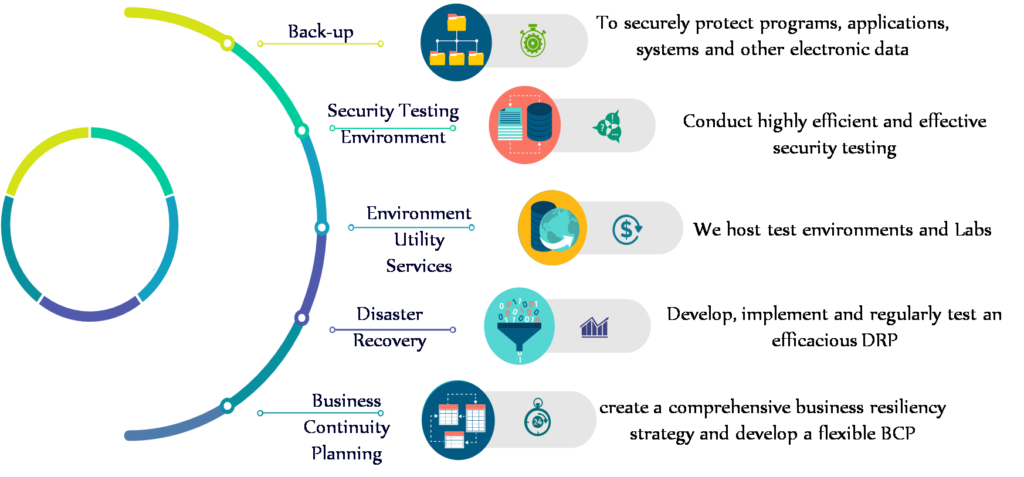
SOC Help Desk Services
- Assisted Help Desk and SOC / NOC for SMEs like Emergency Services, Security Agencies, community Banks, Insurance Brokers and Brokerage firms.
- Employ set of trained security professionals to man a help desk which will be available 24×7 in USA for incident reporting and response management for SMEs on subscription model. Incident response and handling critical incidents desk
- Standard products and solutions to fortify the enterprise security in alliance with leading products available in the market.
- Implementation of in-house SOC / NOC for enterprises and assessment tools etc. will be using off-the-shelf products available in the local USA market or imported if they are not available thru any local agent
- GDRP/FINRA regulations mandate the need to have “Data Protection Officer” (DPO) for many segments of business. PRIAMBA can also provide “DPO as service” using the resources trained for compliance of GDPR leading to sustained revenues.
